For years, ransomware has been plaguing businesses and employees, with complex strains capable of paralyzing entire offices or even entire industries. It’s a virulent malware that typically spreads to computers through malicious emails and encrypts critical files. This is a particularly disturbing threat. The sudden shift in work habits has forced many employees to set up makeshift offices using insecure home networks and shared spaces. Remote workers are more susceptible to these subtle attacks, which exploit daily routines such as opening multiple emails.
Successful ransomware attacks are discouraging because the malware can spread to other computers on the same network, jumping from one device to another and rendering them unusable. Compromised hardware of a remote worker can serve as a launching point into a corporate network. Then, the ransomware actor typically demands a high price to decrypt all files and allow the user or company to resume operations as usual. The latest case of this phenomenon is the case of the global giant JBS, which made headlines in the global press after a ransomware attack, forcing the company to pay $11 million to hackers…

Fig1 : Example of a Situation Conducive to Ransomware Propagation
The article below will provide telecommuters with an overview of how ransomware attacks work, giving them actionable information about vulnerabilities in home setups. We also list prevention guidelines that will help workers avoid the threat altogether.
Comment fonctionnent les attaques de ransomware
Ransomware actors are targeting large-scale victims. They aim to gain access to the corporate network that you might be connected to from your home via a VPN, or to the cloud systems you use or file sharing. Their goal is to propagate through your organization’s network, first to gain access, then to steal and encrypt data.
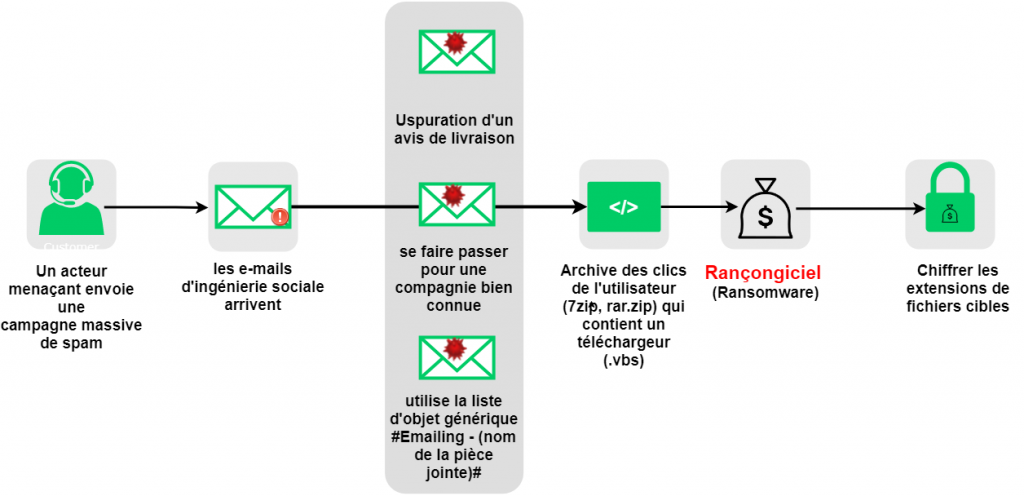
Fig 2. Example of Ransomware Infection Chain
Email phishing is the most commonly used method by ransomware distributors. These malicious actors have become experts in luring unsuspecting users to click on links to websites hosting malware or download dangerous files to initiate the infection process. Here are some methods used by attackers to infect vulnerable home setups:
Attackers can target business email accounts, remote desktop tools (such as Microsoft Remote Desktop or RDP), and cloud-based storage/networks, etc. to deliver the full ransomware payload. This can occur through phishing emails, or they may search for specific tools and then attempt to guess the password (known as a brute-force attack). A new Mac ransomware called EvilQuest includes a keylogger that can capture passwords as you type them, allowing ransomware operators to steal data and use it to spread their malware when you log into a corporate portal.
Attackers can use malware that targets your VPN or remote desktop software. Phishing is again a popular way to do this, or they may hide it in popular software on torrent sites or apps downloaded from app stores.
Attackers can target smart home devices and routers through vulnerabilities and default or simple passwords. Threat actors target these devices to use employees’ home networks as a stepping stone into corporate networks.
Preventing Ransomware
Protecting Against New Ransomware Families
Avoid Disclosing Personal Information
Some malicious actors gather publicly accessible information and use it to gain access to more valuable private information or to deploy malware onto your device. This information often comes from social media sites and public profiles. Be mindful of the type of information you share online – only provide private information when absolutely necessary.
Strengthen Your Passwords
Remote workers should use best password practices for their email and other accounts: use eight characters or more, avoid repeating, sequences, or patterns, and don’t reuse passwords. Since some online business tools and portals may also have default values that attackers can exploit through brute-force attacks, it’s best to regularly change passwords and implement multi-factor authentication. Using a password manager is a good way to store multiple passwords and login credentials in a secure location.
Enable and Display File Extensions
Displaying file extensions is a native Windows feature that shows users what types of files they are opening. Sometimes malicious actors use file names that appear to have two extensions, like “jean.avi.exe.” Users should use this Windows feature to verify what they are opening and avoid any suspicious files.
Open Only Trusted Attachments
Ransomware typically spreads via spam emails with malicious attachments, and many attackers already know the most effective subject lines to grab a user’s attention. They also usually send files in common types – JPEG, Word documents, Excel sheets, and other attachments most offices commonly use. Users should be cautious of email attachments from unknown senders, especially from outside their organization. Some ransomware actors also use unusual files in their spam emails and rely on users simply clicking without looking. Avoid opening suspicious file extensions (like .EXE, .VBS, or .SCR). Some users may even configure their web email servers to block these attachments.
Disconnect from the Internet if the Computer Behaves Suspiciously
Ransomware typically needs to connect to a Command and Control (C&C) server to complete its encryption routine. Without internet access, the ransomware will remain dormant on an infected device. If a user manages to catch the ransomware during the early stages of the attack, they can disconnect from the internet and mitigate damage.
Utilize Security Tools and Features
Many devices and software already come with built-in security features that are regularly updated. Update your home router’s firmware as well as operating systems and software on PCs, mobile devices, and browsers to the latest versions. This includes any virtual tools and VPNs your company provides. All devices should also run up-to-date network and endpoint security solutions from a reputable provider (this should include intrusion prevention, web filtering, spam protection, anti-phishing, and of course, anti-ransomware). Trend Micro Maximum Security provides adequate protection for endpoint devices: PCs, mobiles, and Macs. It can block web threats like ransomware and help you avoid malicious phishing emails
Ransomware Risks
Telecommuters’ systems infected by ransomware will likely lose most of their data if they lack backups and won’t be able to use their machine until a member of the company’s IT team can remove the malware. In the worst cases, the malware will use their machine as a launch point and spread within their company’s network. Recently, ransomware distributors have not only denied their victims access to files, but have also employed double extortion techniques where they steal data and threaten to expose it if victims don’t pay the ransom.
If a ransomware attack succeeds, recovery costs are high. Apart from the loss of valuable data, operations blocked from inaccessible machines significantly impact a company’s bottom line. Not to mention devices might need to be reinstalled or replaced if damaged by the attack. One of the most infamous examples is the incident involving the maritime giant Maersk. The company faced $300 million in business interruption and recovery losses.
The risks of ransomware are serious for both telecommuters and businesses. However, the best way to manage and mitigate the threat is to be vigilant about detecting suspicious online behaviors and following the best practices outlined above. As more and more organizations and employees turn to remote work configurations, securing their work environment should become the new norm.
